ID verification software
The best ID verification software can help your business catch fake IDs, validate data, and better understand your customer.
Use our ID verification tools alone, or embed them into your hardware, software, and fraud prevention workflows.
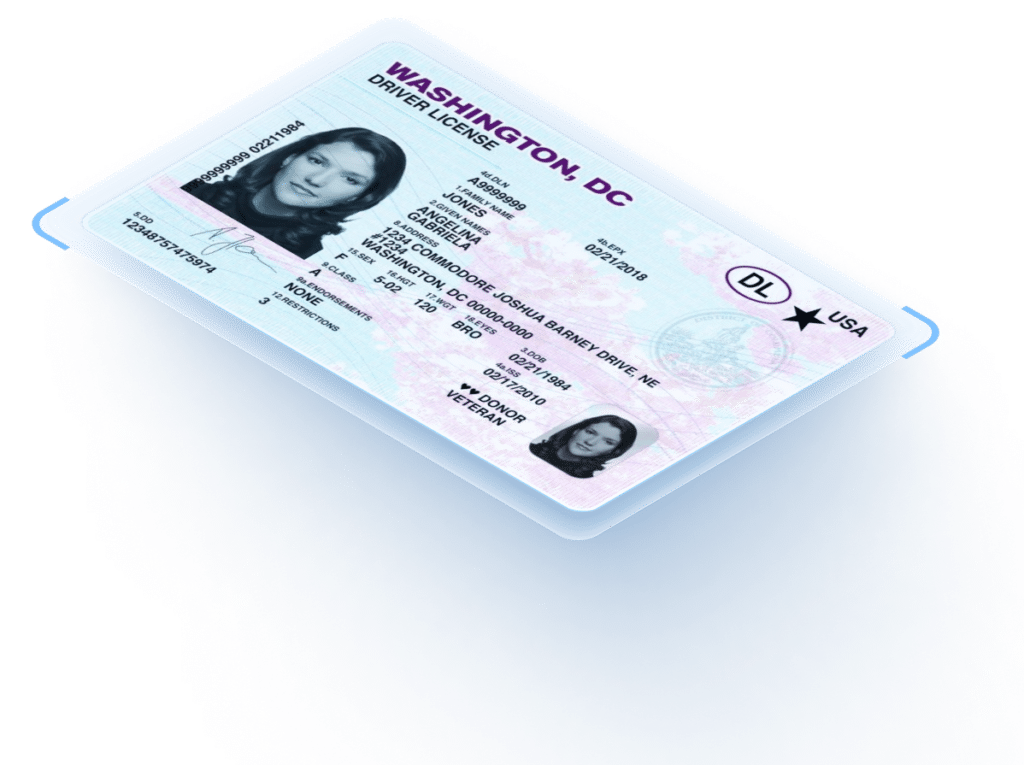
ID verification software helps deter and reduce fraud, meet KYC standards, and reduce loss with layered technology.

Verify IDs & passports
Use our technology to confirm that an ID is legitimate, authentic, and unexpired.

Confirm identity
Ensure that the individual presenting the ID is the legal owner of the document.
ID verification software – remote or in-person
Verify IDs using our Adaptive AI identity tech
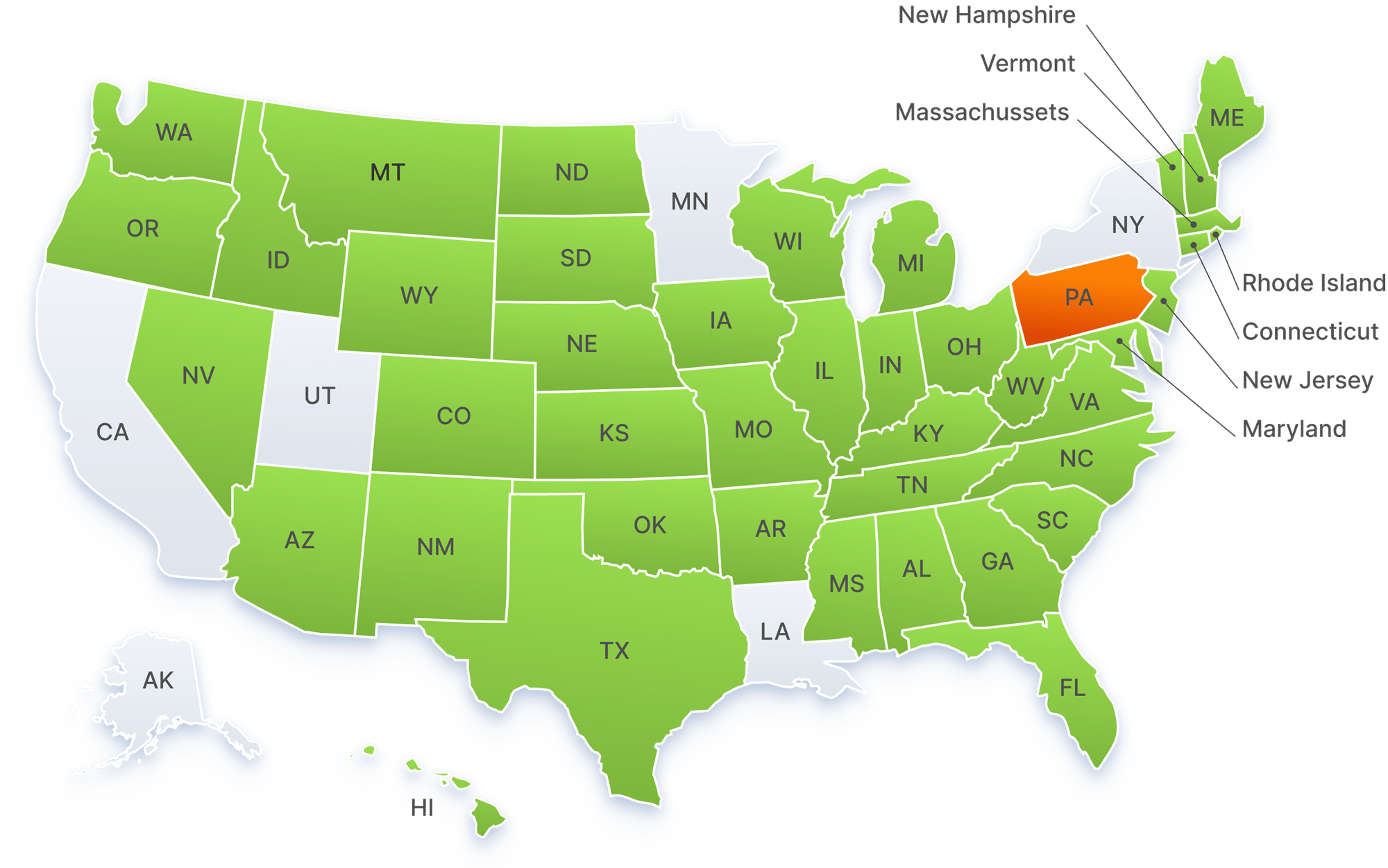
DMV API
Verify IDs by querying the DMV database
Many states allow API access to their DMV for the purpose of verifying whether an ID was issued by the jurisdiction. These checks (also known as AAMVA checks) can help you do a deeper dive on each ID, ensuring that it is legitimate, valid, and matches state records.
ID security features
Verifying an ID using our adaptive AI-platform
It all starts with the scan of an ID – and the verification of that ID. Our ID authentication is so accurate that it often eliminates the need for other expensive technologies.
ID authentication requires specialty hardware capable of simultaneous image capture for front-back crossmatch, multi-wavelength light examination, and AI-driven template checks.
3-light scanning
The ID is scanned using ultraviolet, infrared, and white light to check for the presence or absence of expected markings under multiple light wavelengths.
Hologram/watermark checks
Most IDs contain security features such as holograms, watermarks, and microprints. Our software confirms the presence of these artifacts against known templates.
Front/back matching
We use optical character recognition to read data on the ID and make sure it is a one-to-one match to the date stored in the ID’s 2D barcode – a common “tell” for fake IDs.
Best ID scanners for catching fake IDs
ID scanners improve ID verification software by allowing for rapid capture of images of each ID, examination of the ID under multiple light wavelengths, and AI-driven template checks.
| ID scanner make/model | Thales CR5400 | Thales AT9000 | Thales AT10K | E-Seek M500 |
| Scanner type | Drop-in | Flatbed | Flatbed | Drop-in |
| Scans all North American IDs | ||||
| Scans global passport books | ||||
| Detect expired IDs | ||||
| Age verification (18+, 21+) | ||||
| 2D barcode security checks to catch anomalous PDF417 barcodes | ||||
| Optical character recognition (OCR) for front/back matching | ||||
| Ultraviolet, infrared light scanning | ||||
| Hologram, watermark check capable | ||||
| Capable of catching up to 95% of fake IDs | ||||
| RFID | ||||
| Near field communication (NFC) | ||||
| Image resolution | 300dpi | 400dpi | 550dpi | 600dpi |
| Power source | USB | External | External | External |
| Dimensions | 7″ x 4.25″ x 4.53″ | 7.5″ x 6.4″ 6.2″ | 7.4″ x 6.3″ x 2.6″ | 4.8″ x 5.7″ x 8.5″ |
| Weight | 2.2 lbs | 2.2 lbs | 2.4 lbs | 4.5 lbs |
| Time to authenticate (per ID) – may vary based on system speed | 7.19 seconds | 11.77 seconds | 10.09 seconds | 7.50 seconds |
| Manufacturing location | US / China | China | China | South Korea |
| Data Sheet | ||||
ID Verification Software FAQ
How accurate is ID verification?
ID verification can be performed at a variety of levels. Across all of our products, we use Adaptive AI 2D barcode analysis that is capable of detecting roughly 50-60% of fake IDs.
ID authentication, which performs more in-depth forensic analysis, catches nearly 95% of fake IDs.
Third party checks can then layer on additional measures of security to fully verify each ID or passport.
Can you use a mobile app for ID verification?
Mobile apps can catch some percentage of fake IDs using 2D barcode security checks. 2D barcode security (sometimes called “ID validation”) performs a series of checks on the information on the 2D barcode. These checks are for fake ID “tells” such as mis-spellings, using incorrect abbreviations (ex. shortening Brown to “BWN” instead of “BRN”), size, and location of the barcode. Many low quality fakes cannot pass these barcode security checks, and so apps that read only the 2D barcode (mobile apps and ID scanning software running on a mobile device) can catch these.
However, we have compared the results of some of the most commonly used mobile apps which claim to verify age and detect fakes. They caught less than 35% of the fakes in our library, and some of the apps caught none at all.
How much does ID verification software cost?
ID verification is commonly purchased as our VeriScan software, which offers the full visitor management and age verification software suite in addition to ID authentication. Pricing can be found on the VeriScan web page.
ID authentication can be added to our ParseLink product, for authenticating IDs before data is parsed into your key systems or platforms.
ID authentication can also be licensed via our SDK, and integrated into your system or solution. Pricing varies depending on solution size and scale.
Which ID scanners can perform ID authentication?
ID authentication requires ID scanning hardware that can perform UV, infrared, and white light scanning, front/back matching, and hologram and watermark library checks. We sell the following authentication-capable ID scanning hardware:
- Thales CR5400
- E-Seek M500 (best-in-class)
- Thales AT10K (IDs and passports)
- Thales AT9K (IDs and passports)
Because we know this sophisticated hardware can sometimes present a cost barrier, we sell open-box and certified refurbished scanners at a low price point.
What if a person simply uses another person’s legitimate ID?
ID verification can only tell you whether a document is authentic. Face matching would be required to match the individual present to the ID photo. Usage of an ID that belongs to someone else is called a “false ID.”
How do you verify mobile drivers licenses?
Mobile drivers licenses (mDLs) have their security features embedded into the application itself, typically in the form of biometric access management (fingerprint, face ID). mDLs use an ISO security protocol for data transfer, so that when they are read by any software they are verified.









