At IDScan.net, we pride ourselves on the trust we build between ourselves and our customers. Part of that trust comes from the vigilance and constant improvements being made to our software from a data privacy standpoint. We strive to ensure that our company maintains the highest and most up to date certifications and accreditations, and the latest of those accolades is being SOC 2 compliant.
Our journey to being SOC 2 compliant was completed in 3 major steps. In Fall of 2019, we completed a Readiness Assessment. Then in January 2021, we obtained our SOC 2 Type I report. The final step in achieving compliance came in October 2022 when we were able to complete the SOC 2 Type II audit and obtain our report. By achieving this compliance, we are able to assure our customers that their sensitive information remains safe and protected within our company.
What is SOC 2 compliance?
Service Organization Control 2 (SOC 2) is a subsect of the American Institute of CPAs’ Service Organization, but what does that mean? SOC 2 is a voluntary compliance standard for service organizations, developed by the American Institute of CPAs (AICPA), which specifies how organizations should manage customer data.
It is especially imperative that technology companies are SOC 2 compliant because oftentimes, they are storing information and data in a cloud based environment. Having private data in the cloud can make it more susceptible to data breaches without the proper precautions in place.
What are the two types of SOC 2 reports?
Type I: This report is a standalone snapshot of the company’s control landscape on any given day. This type of audit is designed to assess a vendor’s systems and whether their design is suitable to meet relevant trust principles.
Type II: This report attests to both the design and the operating effectiveness of controls over a defined period of time, usually between 3-12 months.
How to become SOC 2 Certified
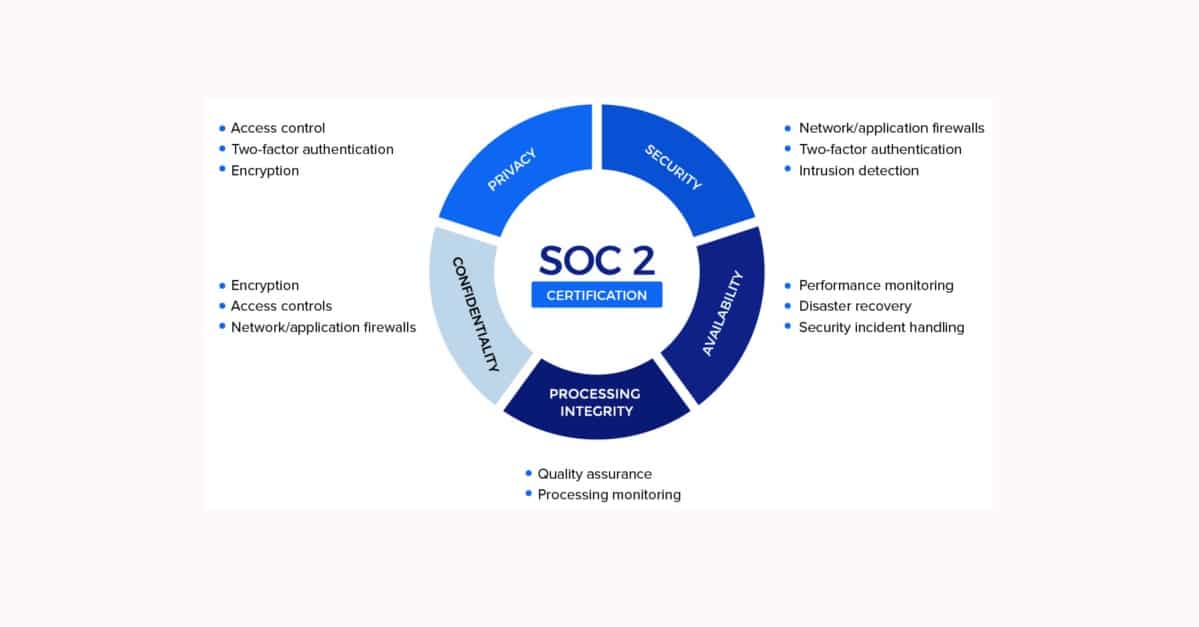
The SOC 2 certification is awarded based on compliance with one or more of the 5 trust principles:
- Security: The company in question must be able to show that their system, and thus their customer’s data, is protected from unauthorized access. By proving this access control, it ensures both the auditor and the customers that measures are in place to prevent misuse, theft, or improper removal of sensitive data.
- Availability: The company being audited must prove that the system has controls in place that ensure the information is available as needed. For example, if the server goes down, there must be measures in place to ensure that the service will be rerouted in a way that makes it available for the end user.
- Processing Integrity: This test is designed to ensure the system is achieving the purpose it was designed to. Especially for software companies, it is critical that the correct data is delivered to the correct customer, and at the correct time.
- Confidentiality: Information that is deemed confidential should have certain protections in place to ensure that the information stays private. These protections must include encryptions that work to protect sensitive information during transmission of said data. A prime example of encryptions are firewalls.
- Privacy: This final principle addresses how a system collects, uses, retains, discloses, and disposes of any personal information in accordance with their privacy notice as well as in accordance with the AICPA’s Generally Accepted Privacy Principles. This principle is particularly important because it protects against the unauthorized access of any personally identifiable information (PII), like race, age, health, sexuality, etc.
Why SOC 2 Compliance is Important
By becoming SOC 2 certified, you are promising your customers that you value their privacy with the utmost regard. You are letting them know that your company has taken every measure necessary to provide them with the services they need, while ensuring that you respect and protect their sensitive information.
At IDScan.net, we strive to comply with all 5 of the trust principles to safeguard our customers’ private information. By being SOC 2 Compliant, we are able to prove to our customers that we do actually implement those security measures that we pride ourselves on.