Certification assures customers of rigorous and independently audited security compliance – SOC 2 compliance – in all IDScan.net solutions
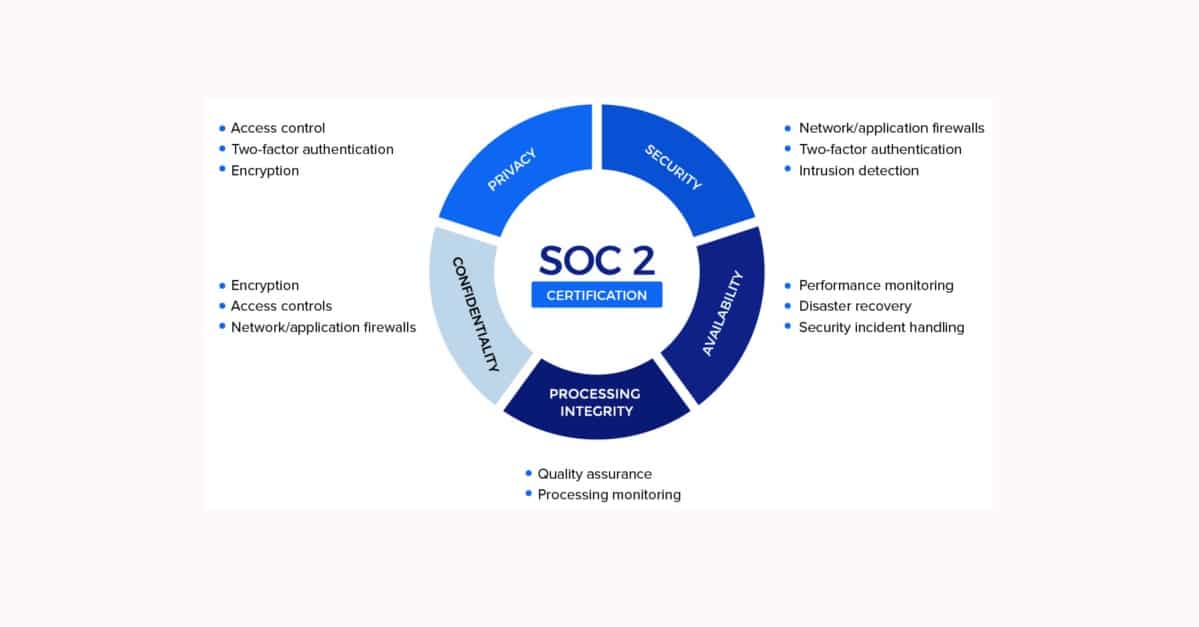
Developed by the American Institute of CPAs (AICPA), SOC 2 defines criteria for managing customer data. These criteria are broken down into five crucial categories: Security, Availability, Processing Integrity, Confidentiality and Privacy. SOC 2 is not just a technical audit, it ensures that our company’s information security measures are consistent with the parameters of today’s cloud requirements.
Certification of compliance is issued and overseen by outside independent auditors to provide partners and customers with verifiable confidence in all IDScan.net solutions. SOC 2 ensures that we are protecting the interests and privacy of our clients by securely managing all data.
Why is it important to IDScan.net & their customers?
For many of our Fortune 1000 clients, especially in the financial, retail, and casino sectors, SOC 2 compliance is not just a bonus- it is a requirement when considering providers. We want to ensure our clients are confident in their decision to trust us with their business.
“We’re incredibly excited about achieving full SOC 2 compliance. It adds a new level to the already high bar of trust and confidence we provide for our customers,” says CEO Denis Petrov. “Ensuring the security and integrity of our customers’ data is paramount and this certification is the ultimate expression of that.”
“Regular audits will ensure ongoing compliance in each of the SOC 2 categories and carry us forward in our vision of creating a safer and smarter world through technology,” Petrov continued.
“Setting and raising industry standards is a passion for each of us at IDScan.net,” said Petrov. “SOC 2 compliance is just another of the many ways we work to earn and retain our clients’ trust.”
How did IDScan.net attain SOC 2 compliance?
The timeline for gaining SOC 2 compliance can vary greatly- taking anywhere from 4 weeks to 18 months. Having a clear strategy and dedicated resources were integral to our success in achieving compliance and staying within our timeline.
Early on in our process, we completed a Readiness Assessment to ensure we were on track and see if we needed to make any changes before the official audit. We also created an extensive Information Security Program, which includes a Third Party Critical Vendor Management policy, an annual review process, and annual company-wide security training specific to our industry and cybersecurity.
Our thorough preparation process, including a combination of technical acumen and top-notch project management, led to our Penetration Test Report coming back with no vulnerabilities noted.
SOC 2 reports are an annual requirement and we are looking forward to ensuring we maintain the system we worked so hard to achieve. We are excited to share our success in this milestone with our clients, who can have peace of mind knowing we take our security practices seriously.